Access
Connect cross-platform accounts & identity management
Permissions are the mechanism used to grant access rights to specific resources within our services. Most AccelByte Cloud service endpoints require permission to be accessed. Our API Documentation (opens new window) lists the permission required for each endpoint, and we also maintain a working list of permission tags (opens new window) for each endpoint, grouped by service.
Permissions are used to filter all access to their respective endpoints, whether it be from users or applications. In the Admin Portal, permissions can be assigned to Clients (opens new window) to determine which endpoints applications and players can access, or to Roles (opens new window) to determine not only which endpoints users can access, but also which features users can access in the Admin Portal itself. So if a user does not have a role that allows them to ban users (opens new window), they will not see that menu when they log into the Admin Portal.
Resources are what permissions are applied to; they are what permissions protect. An example of a resource would be an endpoint URL, such as:
/lobby/v1/public/party/namespaces/{namespace}/parties/{partyId}/attributes
There may be multiple permissions that apply to the same resource, but require different actions. Each endpoint requires a unique permission string.
Permissions can be defined in several places, depending on which users you want to provide the permission to.
A permission consists of a permission tag and permission action.
The permission tag is a string containing multiple tokens, delimited by colons. Permission tags can include details like the namespace and user that the permission applies to, as well as the name of the guarded resource.
Permission actions describe what the permission allows a user or application to do to a resource. The supported actions are Create, Read, Update, and Delete.
Here’s a template of a permission tag:
[ADMIN]:NAMESPACE:namespace:USER:userid:RESOURCENAME
RESOURCENAME This token represents the guarded resource, such as PROFILE or CURRENCY. Permission tags can contain more than one resource name, delimited by colons (e.g., PAYMENT:NOTIFICATION).
If you want to match any resource after userid, replace the resource name with a wildcard * (e.g., [ADMIN]:NAMESPACE:namespace:USER:userid:*).
TIP
There are hundreds of valid permission tags in our Cloud platform. To keep it simple, we keep a working list (opens new window) of all of the permission tags that you can easily copy and paste from.
CAUTION
Some endpoints may not follow the syntax outlined above. To confirm a permission string's syntax, follow the steps below.
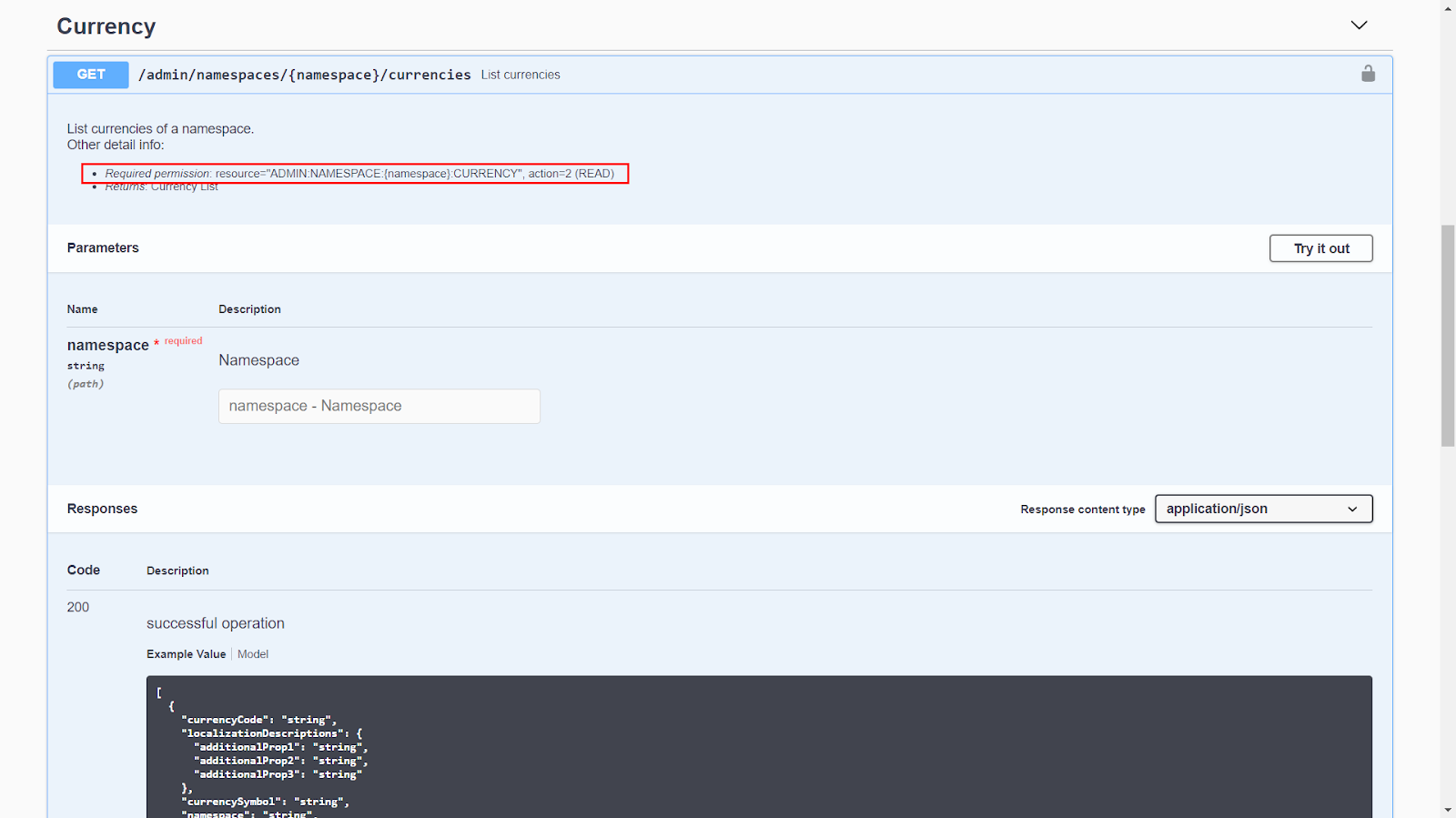
You can see the permission of an endpoint in the AccelByte API Documentation (opens new window).
On the page linked above, click the service for which you need permission.
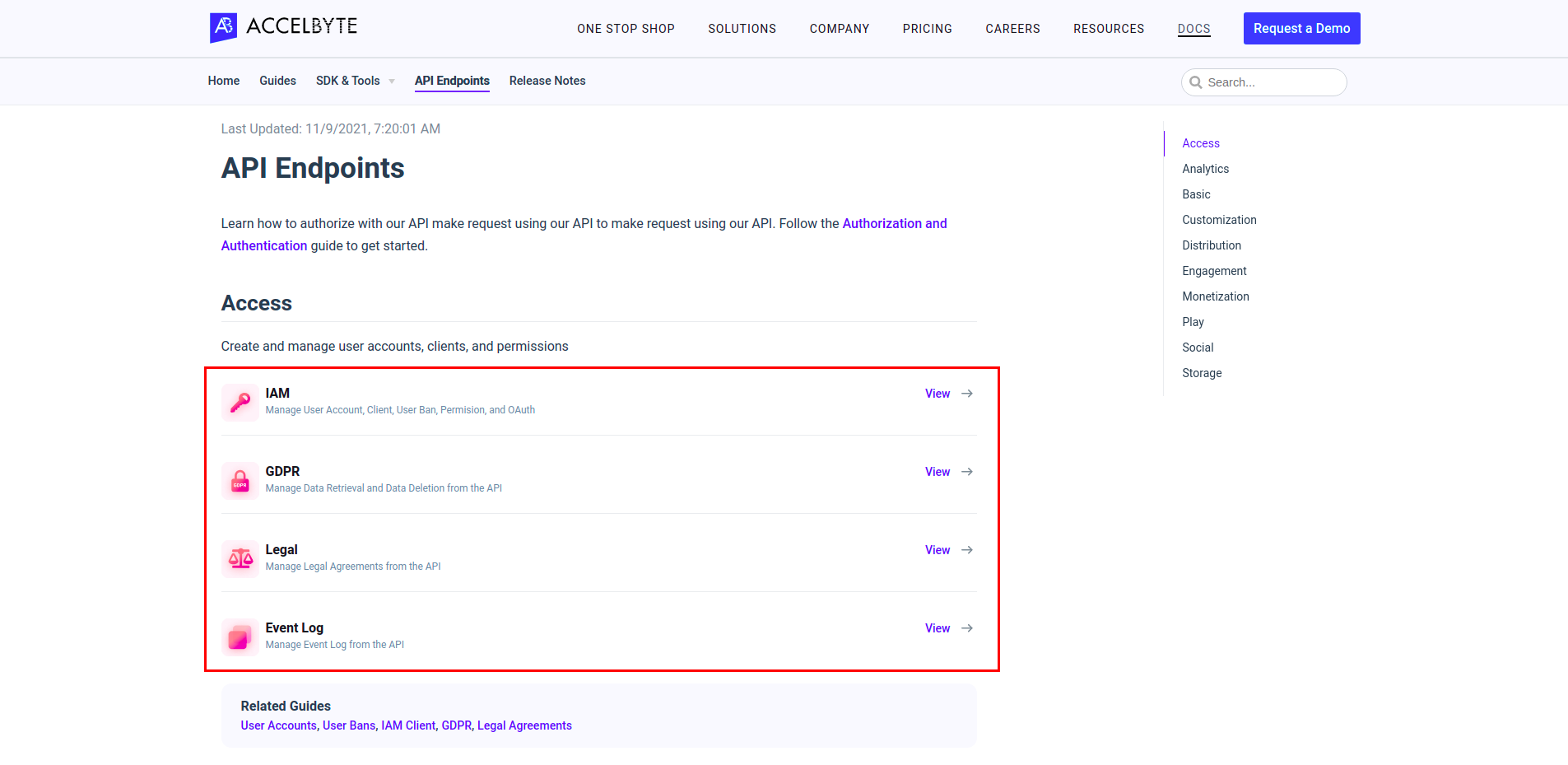
In the Platform APIs page of the selected service, click one of the sub-services to expand the list of available endpoints.
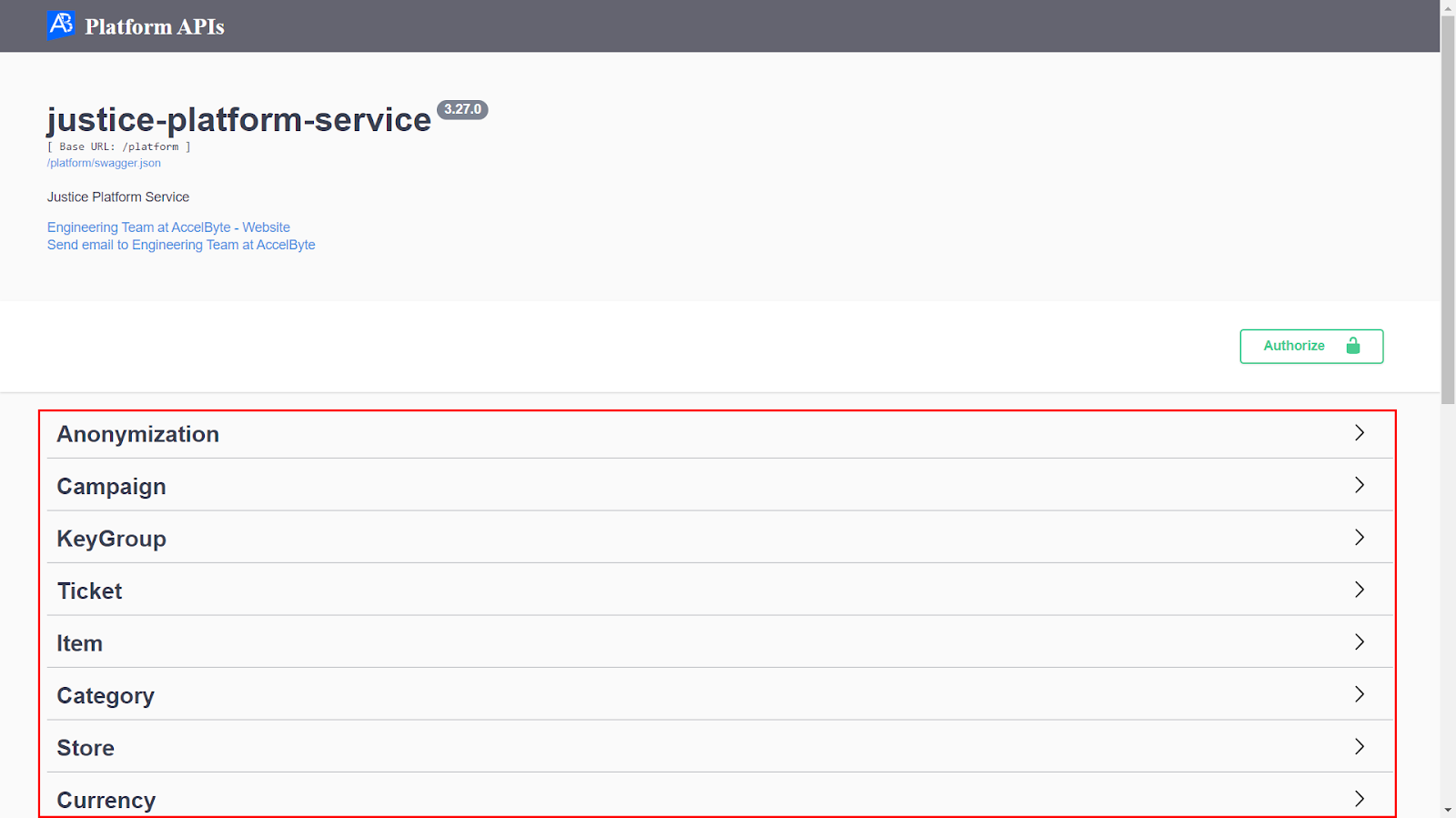
Browse the list of endpoints until you find the one you need, and then click to expand it.
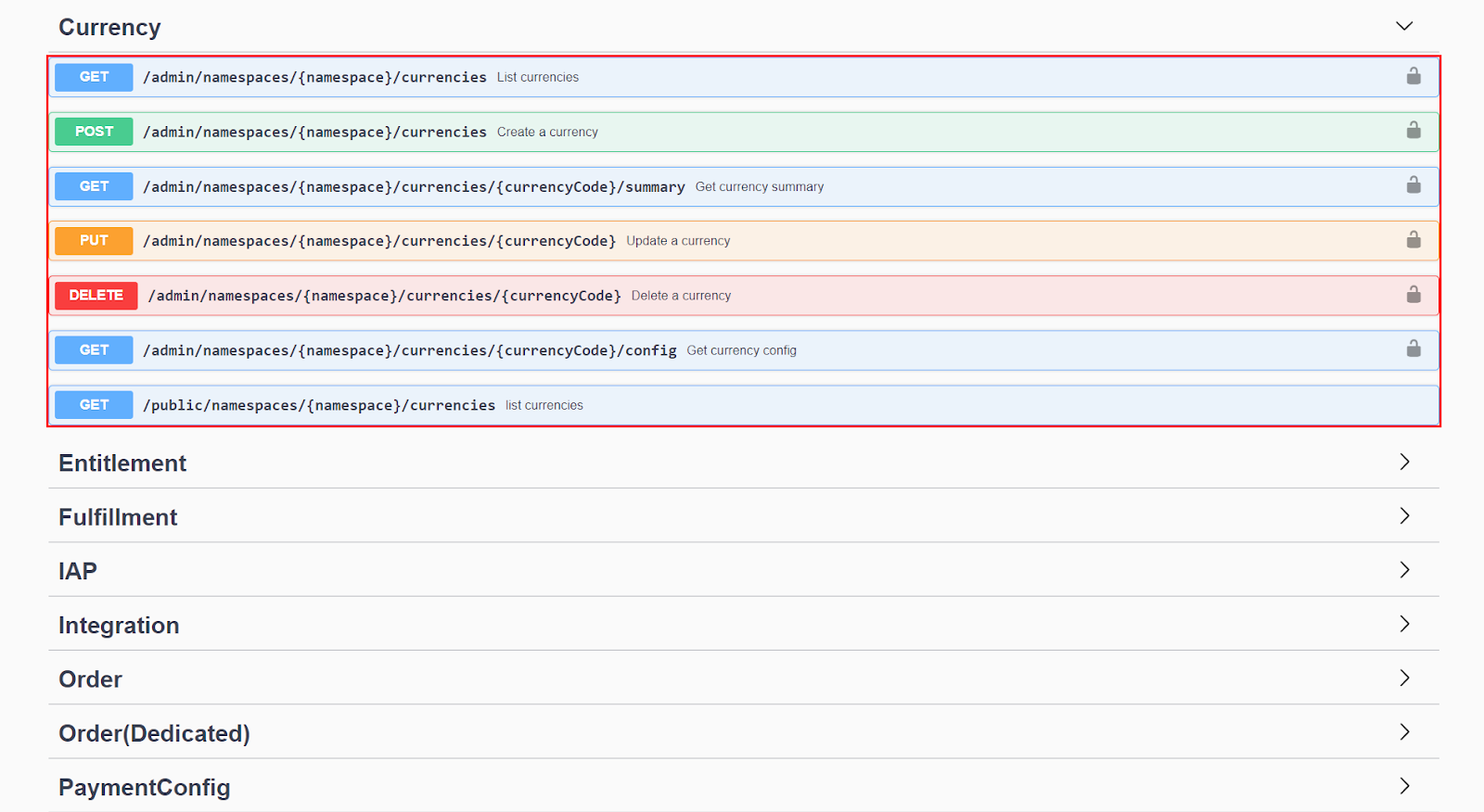
You can see the required permission for the selected endpoint along with its resource and action near the top of the documentation for your endpoint.